This time, however, the situation is somewhat different. It’s not JUST about the price of Bitcoin, or mining profitability, of those forks upon forks which cause hash wars. Yes, people are losing money or, at the very least, not making substantial profits, but there is much more to be lost.
2018 is the year of … mining software?!
Despite the 84% decline so far, 2018 is still the year of crypto mining software, says Kaspersky Labs. Their security bulletin released in November this year states that crypto mining malware is still being heavily distributed by botnets, and even accelerating again after a small decline. So why, you may wonder, would anyone distribute software which generates so little profit? The answer is a really simple one, and the plan ingenious.
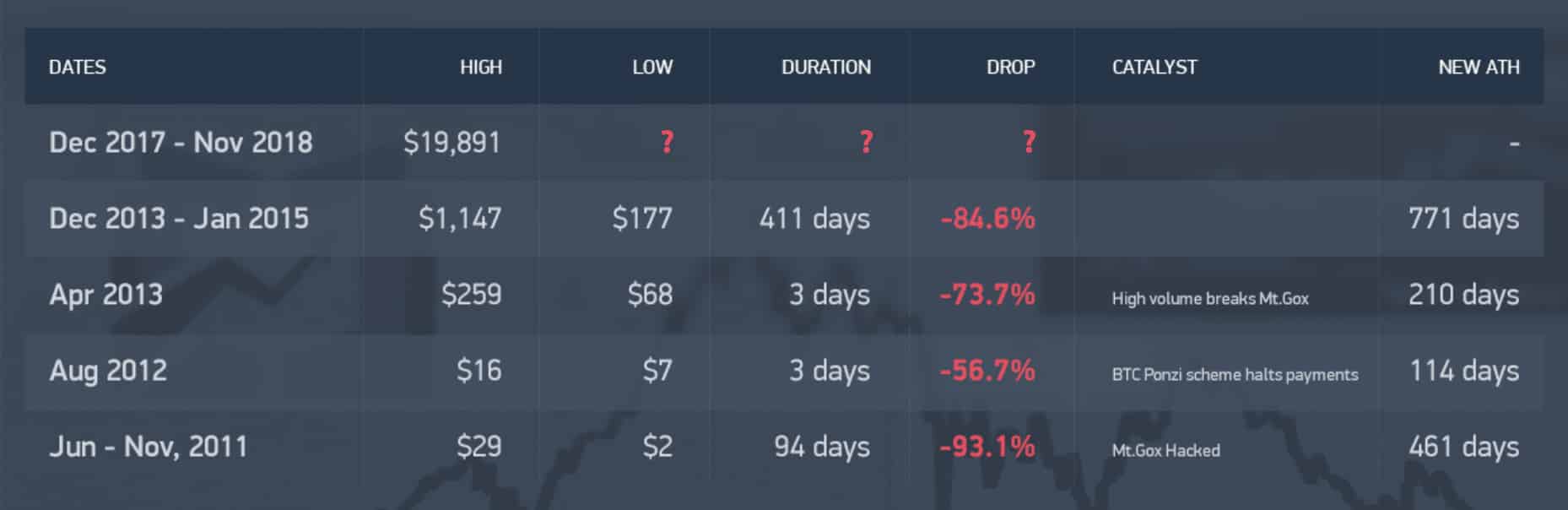
Of course, the current disaster may be yet another blip instead of a bubble burst – we simply don’t know. Each previous downfall, except a 3-day anomaly back in August 2012, was followed by a major bull run, with a few hick-ups on the way, and a huge price increase. In case this happens again, to what new highs could Bitcoin jump from its current ATH of $19,891? The answer is the same: we simply don’t know.
When there is no viable way to predict the turn of events, making an investment in something is no different than simply rolling a dice. In the case of miners, using kilowatts to even megawatts of power to generate only a fraction of the total cost of the operation means being forced to shut down business. Or could anything ever be simply black and white in this shady business?
What if someone else “provided” resources?
To make it simple: if you use someone else’s hardware and someone else’s electricity, and take all the crypto for yourself, that’s even better than having a private fusion reactor. It’s a dream come true for every legitimate businessman out there – doing business in which you invest nothing, yet reap profits. Currently, these profits may not seem all that significant, but if BTC made another huge leap in a couple of years, making thousands of computers mine a couple of Bitcoins for you could easily make you a millionaire in, say, 2025.
Some evil people with good programming skills came up with the plan to do just that, and possibly more.
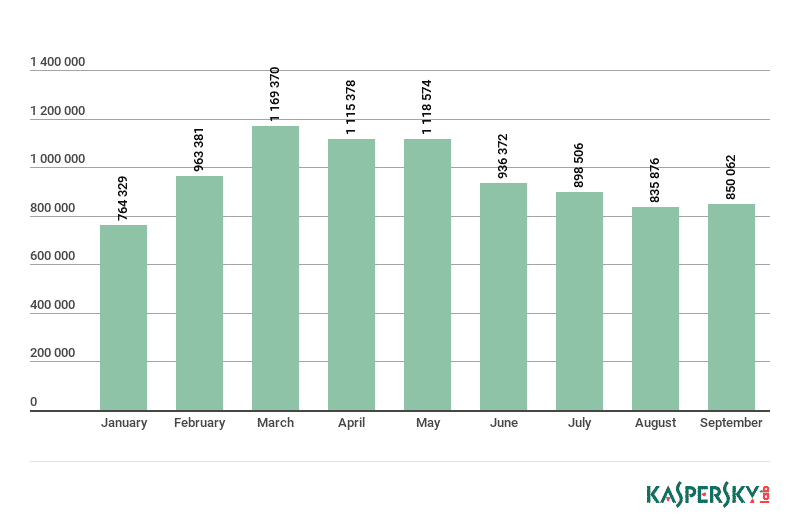
What’s even more interesting is that more users were infected in September than in January making the threat still current. The collapse of 2018 seems to have no negative impact on the infection rate.

Wait, there’s more?
As if things weren’t bad enough already, some people have come up with an even more sinister plan: to pack various spyware and ransomware components or keyloggers inside the mining software, hoping unsuspecting employees would infect servers of corporations or banks. This is social engineering in its purest form: using the acquisitive nature of the people to acquire even more yourself.
Although infecting a server of a large corporation while making it mine crypto for you would probably be a dream come true for botnet operators, their primary penetration vectors are usually small to mid-sized corporations which have a loose security policy. An employee thinks much like a botnet operator, but on a much smaller scale: it can’t possibly hurt to use an idle CPU or GPU at work to make a little “side profit.” At the same time, there is a chance that an inexperienced sysadmin does not see the real threat mining software poses, and only takes low profits it currently generates into consideration, thus enforcing a loose security policy which allows the software to be installed and run.
What happens next is pretty much what any other malware does, aside from momentarily starting to generate profits for the botnet operator: it tries to spread and infect more machines from within the private network. This is an easy part of the task, as computers inside the private network usually trust one another by default. As the number of miners grows, the malware starts logging passwords, stealing emails, application data, and databases and sending them back to the operator.
Finally, the ransomware component kicks in, demanding a crypto transfer and threatening with data disclosure in case the transfer doesn’t take place, all the while still mining and hogging the CPU and GPU. And since the BTC price is currently low, the demand could go as high as 5-10 BTC instead of “just” one back in February of 2018.
Now multiply this by thousands, because that’s how many networks botnets are able to attack at any given moment. The likelihood of success may be low, but the sheer number of attacks makes even a 1% success rate a huge number, which is translated into huge profits. To make things awkwardly funny, these misdeeds are actually a favor to the Bitcoin blockchain and community, because they artificially keep the number of miners at a relatively high level, making transactions cheaper and allowing the Bitcoin to survive.
What can be done about this?
Not much wisdom here: apply a strict security policy. Do not allow users to install software themselves – yes that means not even simple browser add-ons. Configure the firewall to allow communication only on necessary ports and close all the others. Thoroughly scan all the incoming email traffic. Just your usual sysadmin stuff, and you should be safe. Oh yes, one more thing – update the firmware on all your active network equipment, because if it owns a CPU, it can be turned into a miner.
